
This article articulates the steps to immediately take when you’re under attack from this form of attack… something I’ve nicknamed the “Domino Attack”. This attack has distinct phases which the hackers exploit in sequence. Interrupt the sequence as early as possible with evasive action and good training by employees using tools like CyberHoot to help them spot phishing attacks, and to help them protect their passwords religiously! If you’re interested in training your employees visit the CyberHoot.com training website and we’ll connect you to one of our resellers.
Phase 1 of the ‘Domino Breach’:
A client, Finance@IronCladCookware.com received an email from a vendor they regularly deal with that asked them to review a password protected invoice in Google Docs, Drop Box, or other online location. While unusual, the vendor was an important one we deal with regularly so we dutifully complied. Come to find out the vendor’s email domain was off by just one letter (for example: Twirlstool.com email may come from Twrlstool.com – missing an i). The website that we logged into stole one of our employee’s username and password credentials. The hackers now scanned for every unique email address in every folder of that compromised mailbox at our company.
Phase 2: The second Domino to Fall (a look-alike Domain Name is Registered)
In the screen shot below, hackers today registered a look-alike domain name to use in Phase 3. This domain looks very similar to the targeted company’s domain and will be used as home base for these attacks.
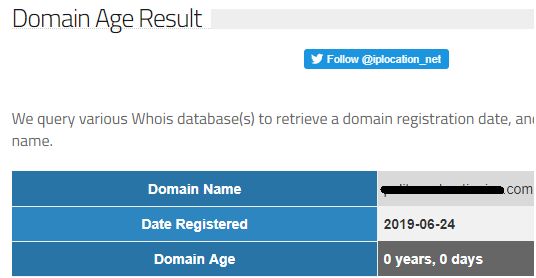
Phase 3: The third Domino – Exploiting Trust Relationships
The hacker then constructs a variety of innocuous but effective emails designed to exploit the trust relationship you have with your vendors, clients, family, and friends by sending it from the imposter email account. In my fictional example: Finance@IroncldCookware.com is used instead of Finance@IroncladCookware.com to email credential stealing attacks to email addresses found within the original compromised email account at IroncladCookware.com. The effectiveness of this attack is found in the fact that the name of the sender is more than likely recognized and accepted by the recipient as a legitimate user. The payload of the attack has a higher likelihood of success because of this implied trust.
Phase 4: Multiple Dominoes begin to Fall across your Contacts
The hackers won’t stop there. Let the email account breaches begin…most people will quickly click on a look-alike email from someone they recognize without a second thought. Fewer will provide credentials to look at an invoice, or outstanding balance or any other plausible financial transaction… leading to ever more companies being breached and ever more companies being targeted. This is known as the Domino Breach effect.
Here is some practical advice on how to protect yourself and how to get in front of the domino’s when your company is part of one of these events!
Step #1: Draw up a quick response email and send to all contacts immediately informing them of the bogus domain and the targeted attacks.
Step #2: Research the ISP of the newly registered domain name and send an abuse complaint about a phishing attack from a look-alike domain name and ask that it be taken down immediately.
Time is of the essence. In the real world, the moment a Look-Alike domain is registered and ready to go, the attack emails begin flowing to all your vendors, clients, friends and family. The domino’s begin to fall as the people who trust you and your name click on the bogus invoice or login request and find themselves compromised.
Sending that warning note to everyone you can think of is a critical and time-sensitive first step.
The rest of these steps need to be taken in increasing order of protection. Not all of these measures cost money. Some are extremely effective protection (thing MFA)
Basic Protection:
Enhanced Protection:
Advanced Protection:
Call to Action:
The basic protection is something all companies need to have in place. Contact CyberHoot today to be connected to a reseller to put your employees through the necessary training to hold the Domino Attack at bay. An ounce of protection is worth a pound of cure. To learn how to protect against similar threats via an email hack, click here
Follow these instructions from CyberHoot on how to recover your breached email account.
Craig, Co-Founder – CyberHoot
Discover and share the latest cybersecurity trends, tips and best practices – alongside new threats to watch out for.

In cybersecurity, not all attacks happen through fancy malware or zero-day exploits. Some of the most effective...
Read more
The rapid rise of generative AI has unlocked enormous promise, but it’s also accelerating the arms race in...
Read more
Newly discovered Android banking Remote Access Trojan (RAT), dubbed Klopatra, has compromised more than 3,000...
Read moreGet sharper eyes on human risks, with the positive approach that beats traditional phish testing.
